AttackTree
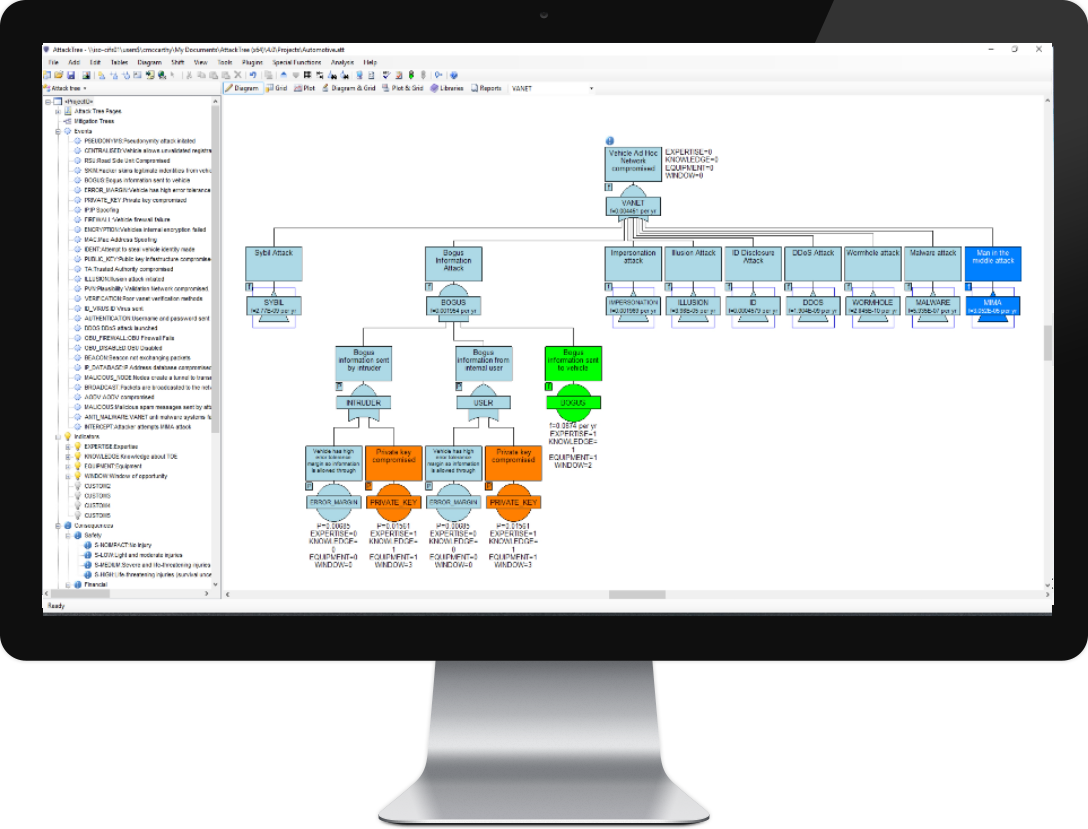
Model system vulnerability, identify weakspots and improve security using threat analysis and attack trees. Construct graphical representations of measures designed to reduce the consequences of a successful attack with mitigation trees.
- Analyze threats according to standards such as ISO 26262, ISO/SAE 21434, J3061, DO-356 and ED-203
- Identify where your system is vulnerable to an attack
- Improve the security of your assets and IT systems
- Model consequence mitigation
- Build models quickly using the advanced GUI features of AttackTree
- Link to Requirements Management tools such as Jama Connect®
Our software has been in continuous development since the 1980s and is the recognized standard for safety and reliability professionals.
Jama Connect® is a registered trademark of Jama Software.
Why choose AttackTree
There are many reasons to choose AttackTree – here are
just a few:
Consequence Driven AttackTrees
AttackTree allows users to define consequences and attach them to any gate within the attack tree. In this way, it is possible to model the consequences of successful attacks on the target system Read More...
Threat Analysis and Risk Assessment
Perform threat analysis and risk assessment according to well-known standards such as
ISO 21434, SAE J3061 and ISO 26262
Read More On Cyber Security Analysis
Read More On Threat Analysis
ISO 21434, SAE J3061 and ISO 26262
Read More On Cyber Security Analysis
Read More On Threat Analysis
Mitigation Trees
Mitigation trees may be used to model the effects of mitigating measures on the consequences resulting from a successful attack Read More...
Contact Sales | Download Free Trial
Why choose Isograph?
Our Credentials
Partners.
Premium Support
Industry Standards
Development
Download Free Trial