Overview
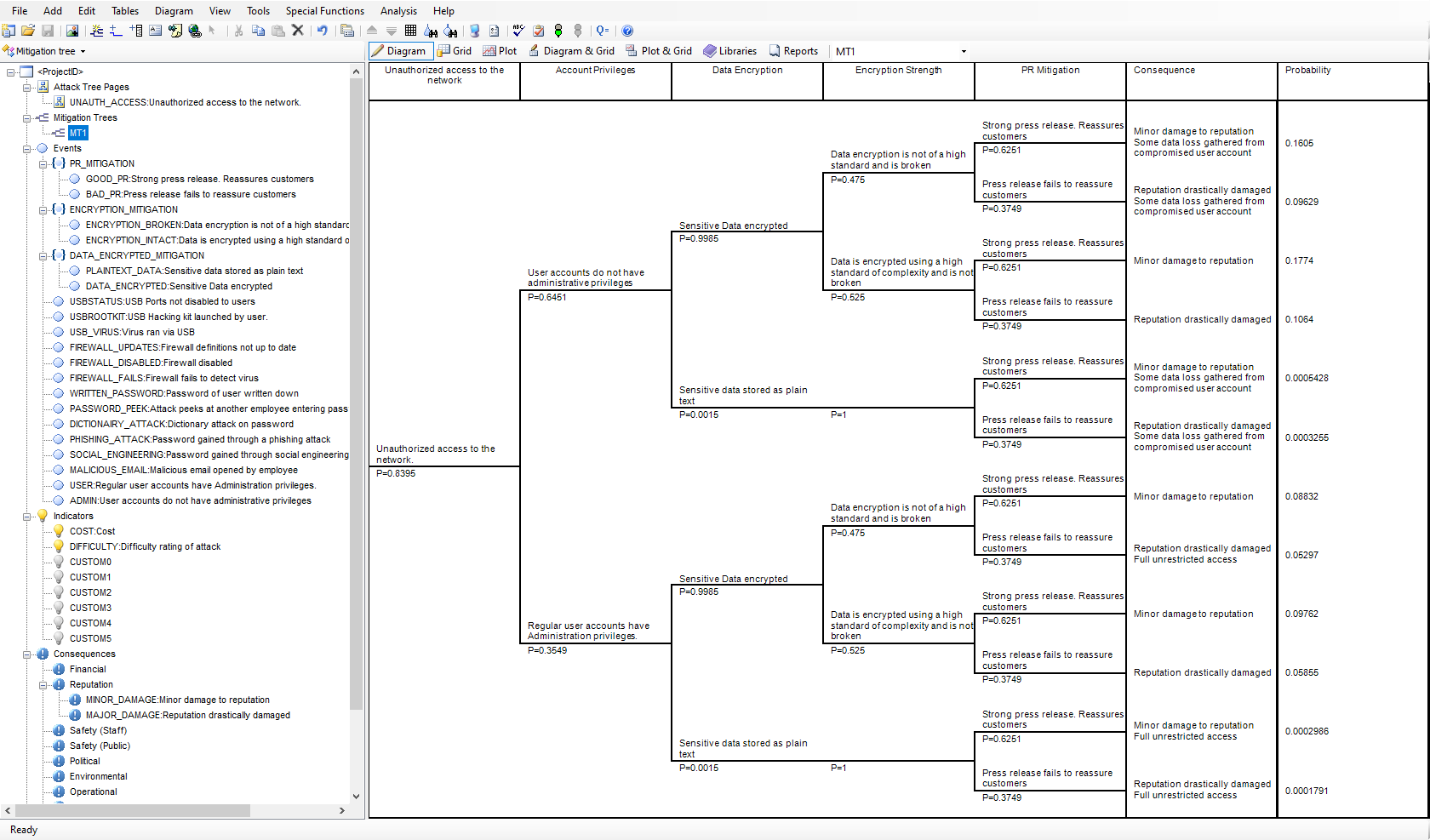
AttackTree may also be used to model the effect of mitigating measures designed to reduce the consequences of a successful attack. Mitigating measures might include procedures for reducing the effects of data breaches, implementing a timely public relations plan or providing rapid emergency response. Mitigating measures may be graphically represented in AttackTree using mitigation trees.
Mitigation Trees
Mitigation trees may be used to model the effects of mitigating measures on the consequences resulting from a successful attack. The initiating event (displayed in the first column of the mitigation tree) usually represents a successful attack or security breach and is usually connected to a TOP gate of an attack tree. The following columns represent the failure or success of measures that affect the consequences arising from the successful attack. These consequences are attached to the end branches of the mitigation tree.